新手一枚,如有错误(不足)请指正,谢谢!! 找个软件一键脱壳,jeb打开搜索就有flag,, 虚拟机指令,看了一下貌似不能逆,,就直接用angr跑了 输出为 这题,挺操蛋 main函数无法F5,改一下栈指针。 解密出来就一个异或运算,不过不全,,,少了5位。
bang
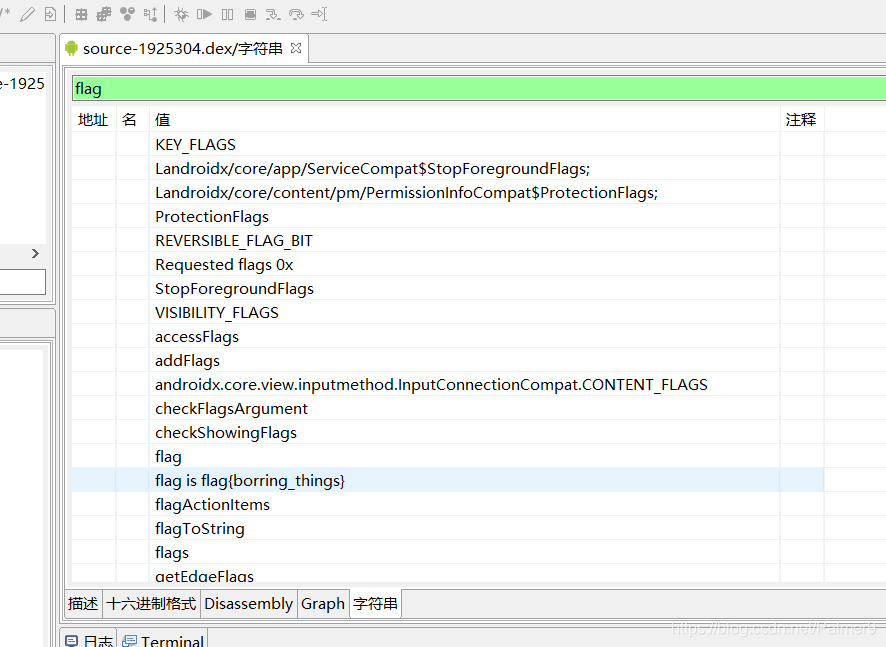
signal
import angr p = angr.Project('/home/cx330/Desktop/Debugging/signal.exe') state = p.factory.entry_state() sm = p.factory.simulation_manager(state) def good(state): return b"good" in state.posix.dumps(1) def bad(state): return b"what" in state.posix.dumps(1) sm.explore(find = good, avoid = bad) if sm.found: find_state = sm.found[0] flag = find_state.posix.dumps(0) print(flag) b'757515121f3d478x00x89)x02xa2x01x8cx00x00x01x00x01x08x02x00x8ax08x00*)x00Ix00x00x1ax00x00x00x02x0ex00Jx1ax0eJx00x00Jx08x02x02x00x8ax00x19' jocker
然后是一个假的验证,验证下面是SMC自解密
附上IDC代码(动调也可以#include <idc.idc> static main() { auto addr = 0x401500; auto i = 0; for(i=0;i<187;i++) { PatchByte(addr+i,Byte(addr+i)^0x41); } }
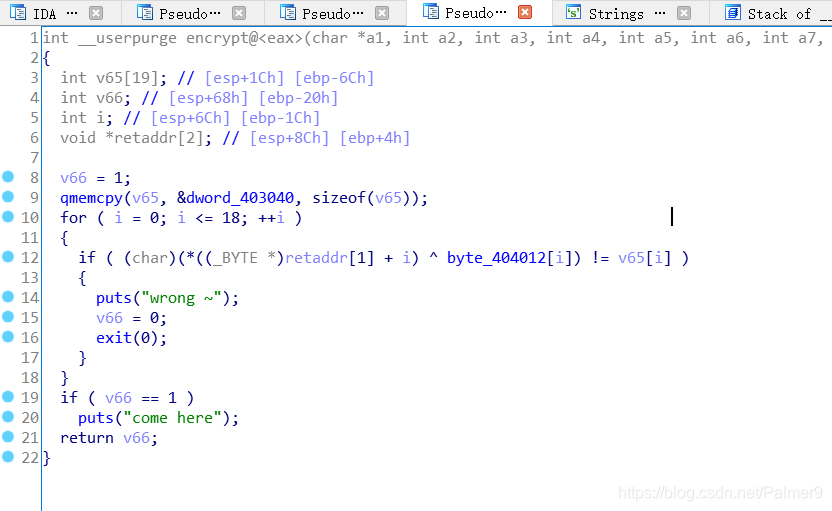
脑洞就很难受
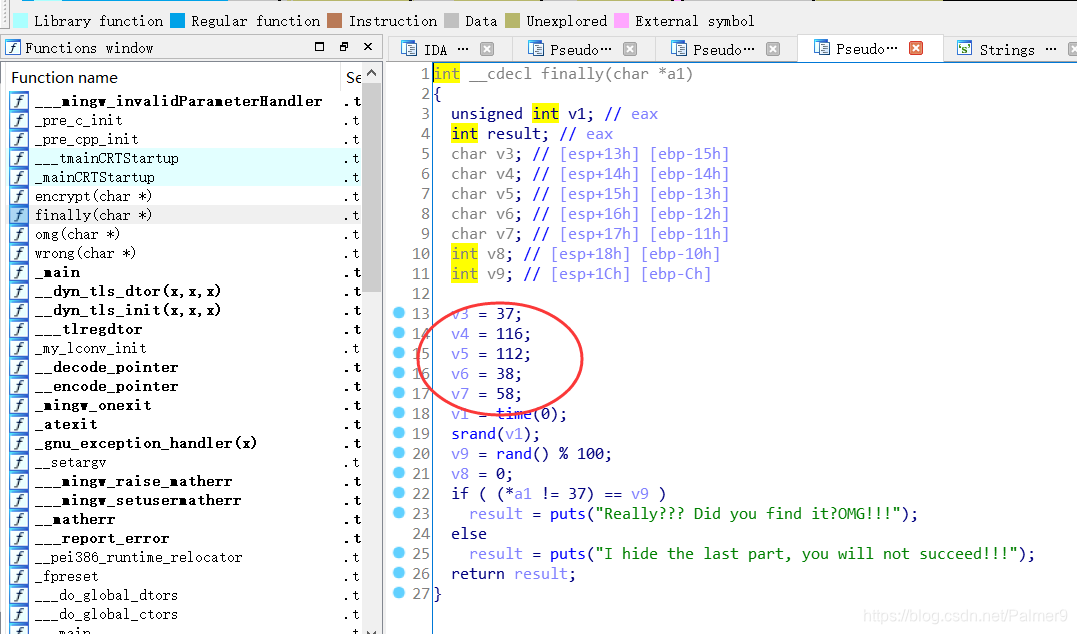
解题脚本#include <stdio.h> #include <string.h> #include "defs.h" unsigned int date[28] = { 0x0000000E, 0x0000000D, 0x00000009, 0x00000006, 0x00000013, 0x00000005, 0x00000058, 0x00000056, 0x0000003E, 0x00000006, 0x0000000C, 0x0000003C, 0x0000001F, 0x00000057, 0x00000014, 0x0000006B, 0x00000057, 0x00000059, 0x0000000D, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000, 0x00000000 }; char str[] = "hahahaha_do_you_find_me?"; int main(void) { int i = 0; char flag[25] = { 0 }; for (i = 0; i < 19; i++) flag[i] = date[i] ^ str[i]; flag[23] = '}'; flag[22] = '}' ^ 58 ^ 38; flag[21] = '}' ^ 58 ^ 112; flag[20] = '}' ^ 58 ^ 116; flag[19] = '}' ^ 58 ^ 37; puts(flag); }
本网页所有视频内容由 imoviebox边看边下-网页视频下载, iurlBox网页地址收藏管理器 下载并得到。
ImovieBox网页视频下载器 下载地址: ImovieBox网页视频下载器-最新版本下载
本文章由: imapbox邮箱云存储,邮箱网盘,ImageBox 图片批量下载器,网页图片批量下载专家,网页图片批量下载器,获取到文章图片,imoviebox网页视频批量下载器,下载视频内容,为您提供.
阅读和此文章类似的: 全球云计算
 官方软件产品操作指南 (170)
官方软件产品操作指南 (170)